Unity Manual
- Unity User Manual 2022.2
- New in Unity 2022.2
- Packages and feature sets
- Released packages
- 2D Animation
- 2D Pixel Perfect
- 2D PSD Importer
- 2D SpriteShape
- 2D Tilemap Extras
- Adaptive Performance
- Addressables
- Ads Mediation
- Advertisement Legacy
- AI Navigation
- Alembic
- Analytics
- Android Logcat
- Animation Rigging
- Apple ARKit XR Plugin
- AR Foundation
- Authentication
- Burst
- CCD Management
- Cinemachine
- Cloud Build
- Cloud Code
- Cloud Diagnostics
- Cloud Save
- Code Coverage
- Collections
- Deployment
- Device Simulator Devices
- Economy
- Editor Coroutines
- FBX Exporter
- Google ARCore XR Plugin
- Input System
- iOS 14 Advertising Support
- JetBrains Rider Editor
- Live Capture
- Lobby
- Localization
- Magic Leap XR Plugin
- Matchmaker
- Mathematics
- Memory Profiler
- ML Agents
- Mobile Notifications
- Multiplay
- Multiplayer Tools
- Netcode for GameObjects
- Oculus XR Plugin
- OpenXR Plugin
- Polybrush
- Post Processing
- ProBuilder
- Profile Analyzer
- Python Scripting
- Recorder
- Relay
- Remote Config
- Scriptable Build Pipeline
- Sequences
- Splines
- Sysroot Base
- Sysroot Linux x64
- System Metrics Mali
- Terrain Tools
- Test Framework
- TextMeshPro
- Timeline
- Toolchain Linux x64
- Toolchain MacOS Linux x64
- Toolchain Win Linux x64
- Tutorial Authoring Tools
- Tutorial Framework
- Unity Distribution Portal
- Unity Profiling Core API
- Unity Transport
- User Generated Content
- User Reporting
- Version Control
- Visual Scripting
- Visual Studio Code Editor
- Visual Studio Editor
- WebGL Publisher
- XR Hands
- XR Interaction Toolkit
- XR Plugin Management
- Release Candidates
- Pre-release packages
- Core packages
- Built-in packages
- AI
- Android JNI
- Animation
- Asset Bundle
- Audio
- Cloth
- Director
- Image Conversion
- IMGUI
- JSONSerialize
- NVIDIA
- Particle System
- Physics
- Physics 2D
- Screen Capture
- Terrain
- Terrain Physics
- Tilemap
- UI
- UIElements
- Umbra
- Unity Analytics
- Unity Web Request
- Unity Web Request Asset Bundle
- Unity Web Request Audio
- Unity Web Request Texture
- Unity Web Request WWW
- Vehicles
- Video
- VR
- Wind
- XR
- Experimental packages
- Packages by keywords
- Unity's Package Manager
- How Unity works with packages
- Concepts
- Configuration
- Package Manager window
- Access the Package Manager window
- List view
- Details view
- Features (detail) view
- Finding packages and feature sets
- Adding and removing
- Install a feature set from the Unity registry
- Install a package from a registry
- Install a package from a local folder
- Install a package from a local tarball file
- Install a package from a Git URL
- Install a package from a registry by name
- Removing an installed package from a project
- Disabling a built-in package
- Switching to another package version
- Importing an Asset Store package
- Updating your Asset Store package
- Remove imported assets from a project
- Delete a package from the Asset Store cache
- Perform an action on multiple packages
- Finding package documentation
- Inspecting packages
- Scripting API for packages
- Scoped registries
- Resolution and conflict
- Project manifest
- Troubleshooting
- Creating custom packages
- Feature sets
- Released packages
- Working in Unity
- Installing Unity
- Upgrading Unity
- API updater
- Upgrade to Unity 2022.2
- Upgrade to Unity 2022.1
- Upgrading to Unity 2021 LTS
- Upgrading to Unity 2020 LTS
- Upgrading to Unity 2019 LTS
- Legacy Upgrade Guides
- Unity's interface
- The Project window
- The Scene view
- The Game view
- Device Simulator
- The Hierarchy window
- The Inspector window
- Editing properties
- The Toolbar
- The status bar
- The Background Tasks window
- Console Window
- Additional windows
- Undo
- Search in the Editor
- Customizing your workspace
- Unity shortcuts
- Quickstart guides
- Advanced best practice guides
- Create Gameplay
- Editor Features
- 2D and 3D mode settings
- Preferences
- Shortcuts Manager
- Build Settings
- Incremental build pipeline
- Project Settings
- Visual Studio C# integration
- RenderDoc Integration
- Editor Analytics
- Check For Updates
- IME in Unity
- Version Control
- Safe Mode
- Command line arguments
- Text-Based Scene Files
- Troubleshooting The Editor
- Analysis
- Memory in Unity
- Profiler overview
- Profiling your application
- Common Profiler markers
- The Profiler window
- Asset Loading Profiler module
- Audio Profiler module
- CPU Usage Profiler module
- File Access Profiler module
- Global Illumination Profiler module
- GPU Usage Profiler module
- Memory Profiler module
- Physics Profiler module
- Physics 2D Profiler module
- Rendering Profiler module
- UI and UI Details Profiler
- Video Profiler module
- Virtual Texturing Profiler module
- Customizing the Profiler
- Low-level native plug-in Profiler API
- Profiling tools
- Log files
- Understanding optimization in Unity
- Asset loading metrics
- Asset workflow
- Input
- 2D game development
- Introduction to 2D
- 2D game development quickstart guide
- 2D Sorting
- Work with sprites
- Create Tilemaps
- Physics 2D Reference
- Graphics
- Render pipelines
- Render pipelines introduction
- Render pipeline feature comparison
- How to get, set, and configure the active render pipeline
- Choosing and configuring a render pipeline and lighting solution
- Using the Built-in Render Pipeline
- Using the Universal Render Pipeline
- Using the High Definition Render Pipeline
- Scriptable Render Pipeline fundamentals
- Creating a custom render pipeline
- Cameras
- Lighting
- Introduction to lighting
- Light sources
- Shadows
- The Lighting window
- Lighting Settings Asset
- The Light Explorer window
- Lightmapping
- The Progressive Lightmapper
- Lightmapping using Enlighten Baked Global Illumination
- Lightmapping: Getting started
- Lightmap Parameters Asset
- Directional Mode
- Lightmaps and LOD
- Ambient occlusion
- Lightmaps: Technical information
- Lightmapping and shaders
- Lightmap UVs introduction
- Lightmap seam stitching
- Custom fall-off
- Realtime Global Illumination using Enlighten
- Light Probes
- Reflection Probes
- Precomputed lighting data
- Scene View Draw Modes for lighting
- Models
- Meshes
- Textures
- Importing Textures
- Texture Import Settings
- Default Import Settings reference
- Normal map Import Settings reference
- Editor GUI and Legacy GUI Import Settings reference
- Sprite (2D and UI) Import Settings reference
- Cursor Import Settings reference
- Cookie Import Settings reference
- Lightmap Import Settings reference
- Directional Lightmap Import Settings reference
- Shadowmask Import Settings reference
- Single Channel Import Settings reference
- Texture Import Settings
- Texture formats
- Mipmaps
- Render Texture
- Custom Render Textures
- Movie Textures
- 3D textures
- Texture arrays
- Cubemaps
- Cubemap arrays
- Streaming Virtual Texturing
- Streaming Virtual Texturing requirements and compatibility
- How Streaming Virtual Texturing works
- Enabling Streaming Virtual Texturing in your project
- Using Streaming Virtual Texturing in Shader Graph
- Cache Management for Virtual Texturing
- Marking textures as "Virtual Texturing Only"
- Virtual Texturing error material
- Sparse Textures
- Loading texture and mesh data
- Importing Textures
- Shaders
- Shaders core concepts
- Built-in shaders
- Standard Shader
- Standard Particle Shaders
- Autodesk Interactive shader
- Legacy Shaders
- Using Shader Graph
- Writing shaders
- Writing shaders overview
- ShaderLab
- ShaderLab: defining a Shader object
- ShaderLab: defining a SubShader
- ShaderLab: defining a Pass
- ShaderLab: adding shader programs
- ShaderLab: specifying package requirements
- ShaderLab: commands
- ShaderLab: grouping commands with the Category block
- ShaderLab command: AlphaToMask
- ShaderLab command: Blend
- ShaderLab command: BlendOp
- ShaderLab command: ColorMask
- ShaderLab command: Conservative
- ShaderLab command: Cull
- ShaderLab command: Offset
- ShaderLab command: Stencil
- ShaderLab command: UsePass
- ShaderLab command: GrabPass
- ShaderLab command: ZClip
- ShaderLab command: ZTest
- ShaderLab command: ZWrite
- ShaderLab legacy functionality
- HLSL in Unity
- GLSL in Unity
- Example shaders
- Writing Surface Shaders
- Writing shaders for different graphics APIs
- Understanding shader performance
- Materials
- Visual effects
- Post-processing and full-screen effects
- Particle systems
- Choosing your particle system solution
- Built-in Particle System
- Using the Built-in Particle System
- Particle System vertex streams and Standard Shader support
- Particle System GPU Instancing
- Particle System C# Job System integration
- Components and Modules
- Particle System
- Particle System modules
- Main module
- Emission module
- Shape module
- Velocity over Lifetime module
- Noise module
- Limit Velocity over Lifetime module
- Inherit Velocity module
- Lifetime by Emitter Speed module
- Force over Lifetime module
- Color over Lifetime module
- Color by Speed module
- Size over Lifetime module
- Size by Speed module
- Rotation over Lifetime module
- Rotation by Speed module
- External Forces module
- Collision module
- Triggers module
- Sub Emitters module
- Texture Sheet Animation module
- Lights module
- Trails module
- Custom Data module
- Renderer module
- Particle System Force Field
- Visual Effect Graph
- Decals and projectors
- Lens flares and halos
- Lines, trails, and billboards
- Sky
- Color
- Graphics API support
- Graphics performance and profiling
- Render pipelines
- World building
- Physics
- Built-in 3D Physics
- Character control
- Rigidbody physics
- Collision
- Introduction to collision
- Continuous collision detection (CCD)
- Create a vehicle with Wheel Colliders
- Physics Debug window reference
- Box Collider component reference
- Capsule Collider component reference
- Terrain Collider component reference
- Wheel Collider component reference
- Mesh Collider component reference
- Sphere Collider component reference
- Physic Material component reference
- Joints
- Articulations
- Ragdoll physics
- Cloth
- Multi-scene physics
- Built-in 3D Physics
- Scripting
- Setting Up Your Scripting Environment
- Scripting concepts
- Important Classes
- Important Classes - GameObject
- Important Classes - MonoBehaviour
- Important Classes - Object
- Important Classes - Transform
- Important Classes - Vectors
- Important Classes - Quaternion
- ScriptableObject
- Important Classes - Time
- Important Classes - Mathf
- Important Classes - Random
- Important Classes - Debug
- Important Classes - Gizmos & Handles
- Unity architecture
- Plug-ins
- Job system
- Multiplayer and Networking
- Multiplayer Overview
- Setting up a multiplayer project
- Using the Network Manager
- Using the Network Manager HUD
- The Network Manager HUD in LAN mode
- The Network Manager HUD in Matchmaker mode
- Converting a single-player game to Unity Multiplayer
- Debugging Information
- Multiplayer Component Reference
- Multiplayer Classes Reference
- Multiplayer Encryption Plug-ins
- UnityWebRequest
- Audio
- Audio overview
- Audio files
- Tracker Modules
- Audio Mixer
- Native audio plug-in SDK
- Audio Profiler
- Ambisonic Audio
- Audio Reference
- Audio Clip
- Audio Listener
- Audio Source
- Audio Mixer
- Audio Filters
- Audio Effects
- Audio Low Pass Effect
- Audio High Pass Effect
- Audio Echo Effect
- Audio Flange Effect
- Audio Distortion Effect
- Audio Normalize Effect
- Audio Parametric Equalizer Effect
- Audio Pitch Shifter Effect
- Audio Chorus Effect
- Audio Compressor Effect
- Audio SFX Reverb Effect
- Audio Low Pass Simple Effect
- Audio High Pass Simple Effect
- Reverb Zones
- Microphone
- Audio Settings
- Video overview
- Animation
- Animation System Overview
- Rotation in animations
- Animation Clips
- Animator Controllers
- Retargeting of Humanoid animations
- Performance and optimization
- Animation Reference
- Animation FAQ
- Playables API
- A Glossary of animation terms
- Legacy Animation System
- Create user interfaces (UI)
- Comparison of UI systems in Unity
- UI Toolkit
- Get started with UI Toolkit
- UI Builder
- Structure UI
- The visual tree
- Structure UI with UXML
- Structure UI with C# scripts
- Custom controls
- Best practices for managing elements
- Encapsulate UXML documents with logic
- UXML elements reference
- UXML element BindableElement
- UXML element VisualElement
- UXML element BoundsField
- UXML element BoundsIntField
- UXML element Box
- UXML element Button
- UXML element ColorField
- UXML element CurveField
- UXML element DoubleField
- UXML element DropdownField
- UXML element EnumField
- UXML element EnumFlagsField
- UXML element FloatField
- UXML element Foldout
- UXML element GradientField
- UXML element GroupBox
- UXML element Hash128Field
- UXML element HelpBox
- UXML element IMGUIContainer
- UXML element Image
- UXML element InspectorElement
- UXML element IntegerField
- UXML element Label
- UXML element LayerField
- UXML element LayerMaskField
- UXML element LongField
- UXML element ListView
- UXML element MaskField
- UXML element MinMaxSlider
- UXML element MultiColumnListView
- UXML element MultiColumnTreeView
- UXML element ObjectField
- UXML element PopupWindow
- UXML element ProgressBar
- UXML element PropertyField
- UXML element RadioButton
- UXML element RadioButtonGroup
- UXML element RectField
- UXML element RectIntField
- UXML element RepeatButton
- UXML element ScrollView
- UXML element Scroller
- UXML element Slider
- UXML element SliderInt
- UXML element TagField
- UXML element TextElement
- UXML element TextField
- UXML element Toggle
- UXML element Toolbar
- UXML element ToolbarBreadcrumbs
- UXML element ToolbarButton
- UXML element ToolbarMenu
- UXML element ToolbarPopupSearchField
- UXML element ToolbarSearchField
- UXML element ToolbarSpacer
- UXML element ToolbarToggle
- UXML element TreeView
- UXML element TwoPaneSplitView
- UXML element UnsignedIntegerField
- UXML element UnsignedLongField
- UXML element Vector2Field
- UXML element Vector2IntField
- UXML element Vector3Field
- UXML element Vector3IntField
- UXML element Vector4Field
- Structure UI examples
- Create list and tree views
- Create a complex list view
- Create a list view runtime UI
- Wrap content inside a scroll view
- Create a tabbed menu for runtime
- Create a pop-up window
- Use Toggle to create a conditional UI
- Create a custom control with two attributes
- Create a slide toggle custom control
- Create a bindable custom control
- Create a custom style for a custom control
- Style UI
- Introduction to USS
- USS selectors
- USS properties
- USS custom properties (variables)
- Apply styles in C# scripts
- Best practices for USS
- Theme Style Sheet (TSS)
- UI Toolkit Debugger
- Control behavior with events
- UI Renderer
- Support for Editor UI
- Create a custom Editor window
- Create a Custom Inspector
- SerializedObject data binding
- Bindable elements reference
- Bindable data types and fields
- Binding system implementation details
- Binding examples
- Bind with binding path in C# script
- Bind without the binding path
- Bind with UXML and C# script
- Create a binding with the Inspector
- Bind to nested properties
- Bind to a UXML template
- Receive callbacks when a bound property changes
- Receive callbacks when any bound properties change
- Bind to a list with ListView
- Bind to a list without ListView
- Bind a custom control
- Bind a custom control to custom data type
- View data persistence
- Support for runtime UI
- Work with text
- Examples
- Migration guides
- Unity UI
- Immediate Mode GUI (IMGUI)
- Unity Services
- Setting up your project for Unity services
- Unity Organizations
- Unity Ads
- Legacy Analytics
- Legacy Analytics: Overview
- Setting Up Legacy Analytics
- Legacy Analytics Dashboard
- Legacy Analytics Events
- Legacy Analytics: Funnels
- Legacy Analytics: Remote Settings
- Unity Analytics A/B Testing
- Monetization
- User Attributes
- Legacy Analytics: Raw Data Export
- Legacy Analytics: Data reset
- Legacy Analytics: COPPA Compliance
- Unity Analytics and the EU General Data Protection Regulation (GDPR)
- Legacy Analytics: Unity Analytics and PIPL
- Analytics Metrics, Segments, and Terminology
- Google Play data safety section for Legacy Analytics
- Unity Cloud Content Delivery
- Unity IAP
- Setting up Unity IAP
- Cross Platform Guide
- Codeless IAP
- Defining products
- Subscription Product support
- Initialization
- Browsing Product Metadata
- Initiating Purchases
- Processing Purchases
- Handling purchase failures
- Restoring Transactions
- Purchase Receipts
- Receipt validation
- Store Extensions
- Cross-store installation issues with Android in-app purchase stores
- Store Guides
- Implementing a Store
- Unity Cloud Diagnostics
- Unity Integrations
- Multiplayer Services
- Unity Distribution Portal
- Unity Accelerator
- XR
- Getting started with AR development in Unity
- Getting started with VR development in Unity
- XR Plug-in Framework
- Configuring your Unity Project for XR
- Universal Render Pipeline compatibility in XR
- Unity VR project template
- Unity AR project template
- XR API reference
- Single Pass Stereo rendering (Double-Wide rendering)
- VR Audio Spatializers
- VR frame timing
- Unity XR SDK
- Unity's Asset Store
- Asset Store packages
- Publishing to the Asset Store
- Creating your Publisher Account
- Creating a new package draft
- Deleting a package draft
- Uploading assets to your package
- Filling in the package details
- Submitting your package for approval
- Viewing the status of your Asset Store submissions
- Collecting revenue
- Providing support to your customers
- Adding tags to published packages
- Connecting your account to Google Analytics
- Promoting your Assets
- Refunding your customers
- Upgrading packages
- Deprecating your Assets
- Issuing vouchers
- Managing your publishing team
- Asset Store Publisher portal
- Platform development
- Using Unity as a Library in other applications
- Deep linking
- Xcode frame debugger Unity integration
- Android
- Introducing Android
- Getting started with Android
- Developing for Android
- Android mobile scripting
- Input for Android devices
- Android application size restrictions
- Graphics for Android
- Testing and debugging
- Create and use plug-ins in Android
- Integrating Unity into Android applications
- Deep linking on Android
- Android thread configuration
- Device features and permissions
- Building and delivering for Android
- ChromeOS
- Dedicated Server
- iOS
- Introducing iOS
- Getting started with iOS
- Developing for iOS
- Building and delivering for iOS
- Troubleshooting on iOS devices
- Reporting crash bugs on iOS
- Linux
- macOS
- tvOS
- WebGL
- WebGL Introduction
- Getting started with WebGL development
- WebGL Development
- WebGL native plug-ins for Emscripten
- Memory in Unity WebGL
- Cache behavior in WebGL
- Interaction with browser scripting
- Input in WebGL
- Debug and troubleshoot WebGL builds
- WebGL performance considerations
- WebGL Networking
- Cursor locking and full-screen mode in WebGL
- WebGL browser access to device features
- Build and distribute a WebGL application
- Windows
- Universal Windows Platform
- Introduction to Universal Windows Platform
- Get started with Universal Windows Platform
- Develop for Universal Windows Platform
- Build and deliver for Universal Windows Platform
- Unity Search
- Legacy navigation and pathfinding
- Navigation Overview
- Navigation System in Unity
- Inner Workings of the Navigation System
- Building a NavMesh
- Advanced NavMesh Bake Settings
- Creating a NavMesh Agent
- Creating a NavMesh Obstacle
- Creating an OffMesh Link
- Building OffMesh Links Automatically
- Building Height Mesh for Accurate Character Placement
- Navigation Areas and Costs
- Loading Multiple NavMeshes using Additive Loading
- Using NavMesh Agent with Other Components
- Navigation Reference
- Navigation How-Tos
- Navigation Overview
- Glossary
- Unity User Manual 2022.2
- Platform development
- macOS
- Build and distribute a macOS application
- Code sign and notarize your macOS application
Code sign and notarize your macOS application
This page details the process of code signing and notarization for macOS applications.
Code signing is the process of creating a code signature for an application. This signature guarantees the integrity of applications and safeguards from any tampering. Apple devices use an application’s code signature to detect changes made after the code signature was created. If an application doesn’t have a code signature, the device warns the end user before they open it. Unity automatically code signs any application it builds for macOS.
Notarization is when Apple verifies your application to ensure it has a Developer ID code signature and doesn’t contain malicious content. For more information about notarization, refer to Apple’s documentation on macOS Code Signing in Depth and Notarizing macOS Software Before Distribution.
If you develop on an Apple device, you can use Xcode, Xcode command-line tools, or Unity Cloud BuildA continuous integration service for Unity projects that automates the process of creating builds on Unity’s servers. More info
See in Glossary to notarize your application. If you don’t have an Apple device, use Unity Cloud Build.
This page has information on the following notarization methods:
- Notarization using Xcode
- Notarization using Xcode command-line tools
- Notarization using Unity Cloud Build
Note: Notarization isn’t required to distribute your application through the Mac App Store. The Mac App Store’s upload process includes similar content validation to notarization. Refer to Delivering to the Mac App Store for more information.
Use Xcode to notarize your application
Unity can create an Xcode project that represents your Unity project during the build process. You can use this Xcode project to notarize your application. Follow the macOS application build steps to create an Xcode project from your Unity project. For information on notarizing the Xcode project, see Apple’s documentation on Notarizing macOS Software Before Distribution.
Use Xcode command-line tools to notarize your application
If you can’t notarize your application in the Xcode environment or want to control notarization manually, you can use Xcode’s command-line tools. To do this, you need the following:
- An Apple ID.
- An Apple device that runs macOS 10.15 Catalina or later.
- Xcode 11 or later. This installs the required command-line tools.
- An Apple Developer Program membership. If you don’t have an Apple Developer membership, sign up at Apple Developer.
Code sign your application
To notarize your application with the Xcode command-line tools, you must first code sign the application. This section explains how to code sign your application using Xcode’s command-line tools.
Signing identity
Unity adds a code signature to every macOS build it produces. This simple code signature doesn’t identify you as the developer. To notarize an application, Apple requires the code signature to include a cryptographic signature that identifies the developer. This is called a signing identity. Usually, you use a Developer ID certificate.
To create a new Developer ID certificate, go to Create a New Certificate:
- Follow the prompts to create a private key and upload a Certificate Signing Request.
- Download your Developer ID certificate. The file format for this certificate is
.cer. - Click on the certificate to add it to your Keychain. Within the Keychain, it appears with a name formatted like: Developer ID Application : XXX (YYY).
Application identifier
To notarize your application, Apple needs to identify it. There are two ways to get the application identifier: in Unity, or in the built application’s information property list file.
- In Unity:
- Go to Edit > Project Settings > Player.
- Expand the Other Settings section and go to Mac App Store Options.
- See the value of Bundle Identifier.
- In the information property list file:
- In the Finder, go to your built application.
- Right-click on the application and select Show Package Contents.
- Go to Contents and open Info.plist.
- The key that represents the application identifier is CFBundleIdentifier.
When you have your application identifier, you can register it with Apple. To do this:
- Go to Apple Developer and log in.
- Select Certificates, IDs & Profiles.
- Select Identifiers
- Add your bundle ID.
Entitlements
Entitlements are permissions or restrictions your code signature includes that allow or prevent your application from taking specific actions.
To set entitlements for your application:
- In the same directory as your built application, create a file with the same name as your application with the
.entitlementsfile extension. For example, if your application is called Sample, create a file calledSample.entitlements. - Open the file with a text editor and copy in the following content:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.security.cs.disable-library-validation</key>
<true/>
<key>com.apple.security.cs.disable-executable-page-protection</key>
<true/>
</dict>
</plist>
These entitlements are the minimum entitlements a macOS application requires to have a Hardened Runtime. If your application requires any more entitlements, add them to this list.
Code sign an application
The code signing process uses the command line. To start, open Terminal and navigate to the directory that the application is in. To ensure that you have the necessary read permissions to process code signing, run the following command where "application_name.app" is the name of your application:
chmod -R a+xr "application_name.app"
A code signature uses a particular signing identity. Usually, this is your Developer ID Application signing identity. However, some digital distribution services, such as the Mac App Store require a different signing identity.
To code sign your application, run the following command where:
-
"application_name.app"is your built application. - `“application_name.entitlements” is the name of the entitlements file.
-
"Developer ID Application : XXX (YYY)"is your signing identity.
codesign --deep --force --verify --verbose --timestamp --options runtime --entitlements "application_name.entitlements" --sign "Developer ID Application : XXX (YYY)" "application_name.app"
This command recursively navigates through the application bundle folder, signs all files, adds a secure timestamp, and embeds the entitlements you’ve set into the signature.
Warning: Using the --deep option might cause issues with your code signature. This is because:
It applies the same code signing options and entitlements to all the code that it signs.
It only signs code files that it finds. If there are code files in a place where the system expects to find data, using
--deepdoesn’t sign these code files.
For more information about the --deep option and how to resolve issues with it, refer to Sign your code.
Upload an application for notarization
After you code sign your application, you must upload it to Apple for notarization. To fulfill the upload requirements, the following items are necessary:
Compress the application
Apple requires that you compress your application before you upload it for notarization. To do this:
Open Terminal and navigate to the directory the application is in.
- Run the following command where:
-
"application_name.app"is your built application. -
"application_name.zip"is the name of the compressed file to generate.
-
ditto -c -k --sequesterRsrc --keepParent "application_name.app" "application_name.zip"
This compresses your application and outputs the compressed file to the same directory as your application.
Generate an application password
To notarize an application, Apple requires a unique password in a particular format. To generate an application password, you need to have an Apple ID. If you don’t have one, go to Manage your Apple ID and create one.
For information on how to generate an application password, refer to How to generate an app-specific password. The password you generate uses the following format: xxxx-xxxx-xxxx-xxxx.
Retrieve your provider short name
A provider short name is a single-word label that identifies an individual or a company. Apple uses a provider short name to determine which organization to notarize for when your Apple ID is associated with more than one organization. To get your provider short name:
- Open Terminal.
- Run the following Xcode command where:
-
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password.
-
xcrun iTMSTransporter -m provider -u apple_id -p xxxx-xxxx-xxxx-xxxx
Start the upload process
For Apple to notarize your application, you need to upload it to their notarization servers. To do this:
- Open Terminal and navigate to the directory the compressed application is in.
- Run the following command where:
-
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password. -
provider_short_nameis your provider short name. -
application_bundle_idis the application’s application identifier. -
application_name.zipis the compressed application.
-
xcrun altool --notarize-app --username apple_id --password xxxx-xxxx-xxxx-xxxx --asc-provider provider_short_name --primary-bundle-id application_bundle_id --file application_name.zip
If the upload is successful, Apple displays a response in Terminal that contains a request ID. You can use this request ID to check on the status of your request. This is useful because the notarization process might take multiple hours depending on the traffic to the service. To do this:
- Open Terminal and navigate to the directory the compressed application is in.
- Run the following command where:
-
request_idis the request ID that Apple returns from the previous command. -
apple_idis your Apple ID. -
xxxx-xxxx-xxxx-xxxxis your application password. -
provider_short_nameis your provider short name.
-
xcrun altool --notarization-info request_id --username apple_id --password xxxx-xxxx-xxxx-xxxx --asc-provider provider_short_name
When the notarization process is complete, Apple sends you a confirmation email at the address associated with your Apple ID. You can then verify that notarization was successful. To do this:
- Open Terminal and navigate to the directory the application is in.
- Run the following command where:
-
application_name.appis the name of your application:
-
spctl -a -v application_name.app
If notarization was successful, this returns a message that indicates that Apple accepted the application and includes your Developer ID.
Staple the application
After notarizing your application, any device that runs it can verify that it has a code signature and contains no malicious content. However, the device can only perform this verification online. To verify your application on a device without an internet connection, you must staple the application. For information about stapling, refer to Staple the Ticket to Your Distribution.
To staple your application,
- Open Terminal and navigate to the directory the application is in.
- Run the following command where
"ApplicationName.app"is the name of your application:xcrun stapler staple "ApplicationName.app".
Notarization using Unity Cloud Build
Unity Cloud Build can notarize and staple your macOS application during the build process. To do this, Unity requires the following:
- An Apple ID.
- An application-specific password.
- An Apple Developer Program membership.
- An entitlements file.
- A Developer ID certificate exported in the PKCS #12 Personal Information Exchange (.p12) file format.
- The password you used to create the
.p12file. - Your provider short name.
Depending on the platform you are developing on, the process for some of these requirements differs. If you develop on an Apple device, you can use Xcode command-line tools to get the information and create the relevant files. If you develop on Windows or Linux, you won’t have access to Apple-specific Xcode command-line tools.
Regardless of which platform you use, the process to get the Apple ID, password, and entitlements files are platform-agnostic:
- If you don’t have an Apple ID, go to Manage your Apple ID and create one.
- Create an application password. For information on how to do this, refer to Generating an application Password.
- If you don’t have an Apple Developer membership, sign up at Apple Developer.
- Create an entitlements file for your application. For information on how to do this, refer to Entitlements.
After you complete these steps:
- If you are developing on macOS, see Unity Cloud Build notarization for Apple devices.
- If you are developing on Windows or Linux, see Unity Cloud Build notarization for Windows and Linux devices.
Unity Cloud Build notarization for Apple devices
If you develop on an Apple device, you can use Xcode command-line tools to meet the requirements listed in Notarization using Unity Cloud Build. You can then set up Unity Cloud Build to notarize and staple your application as part of the build process. To meet the requirements:
- Follow the platform-agnostic steps in Notarization using Unity Cloud Build.
- Create a Developer ID certificate and add it to your Keychain. For information on how to do this, refer to Signing identity.
- Export the Developer ID certificate from the Keychain as a file in Personal Information Exchange (
.p12) format. For information on how to do this, refer to Import and export keychain items using Keychain Access on Mac. - Get your provider short name. For information on how to do this, refer to Getting your provider short name.
After you meet the requirements, fill out and submit the Unity Cloud Build notarization form.
Unity Cloud Build notarization for Windows and Linux devices
If you develop on Windows or Linux and want to build, notarize, and staple your application for macOS, you can’t use Xcode command-line tools. To meet the requirements listed in Notarization using Unity Cloud Build to set up Unity Cloud Build to notarize and staple your application as part of the build process:
- Follow the platform-agnostic steps in Notarization using Unity Cloud Build.
- Create a Developer ID certificate and download it. For information on how to do this, refer to Signing identity. Note: The last step in Signing identity is only relevant for macOS users.
- Convert the Developer ID certificate to the PKCS #12 Personal Information Exchange (.p12) file format. For information on how to do this, refer to Converting a Developer ID certificate to a .p12 file on Windows and Linux.
- Get your provider short name through your Apple Developer account. To do this, go to Membership Details and find your Team ID. You can use the Team ID as a provider short name.
After you meet the requirements, fill out and submit the Unity Cloud Build notarization form.
Convert a Developer ID certificate to a .p12 file on Windows and Linux
A .p12 file bundles both your Developer ID certificate and a private key. To create one from your Developer ID certificate:
Open a command-line interface and go to the directory that contains your Developer ID certificate file. If you didn’t download your Developer ID certificate, refer to Signing identity.
- Developer ID certificates use the
.cerfile format. Convert this file to the.pemfile format. To do this, run the following command where:-
developer_identity.ceris the Developer ID certificate file to convert. -
developer_identity.pemis the file name and file type to output.
openssl x509 -in developer_identity.cer -inform DER -out developer_identity.pem -outform PEM -
- Generate a new private key. To do this, run the following command where:
-
mykey.keyis the file name of the private key to output.
openssl genrsa -out mykey.key 2048 -
- Generate the
.p12file. To do this, run the following command where:-
mykey.keyis the private key file you generated in step 3. -
developer_identity.pemis the.pemfile you generated in step 2.
openssl pkcs12 -export -inkey mykey.key -in developer_identity.pem -out iphone_dev.p12 -
Submit the Unity Cloud Build notarization form
After you meet the requirements outlined in Notarization using Unity Cloud Build, follow these steps to setup Unity Cloud Build notarization:
- Set up your project to use Unity Cloud Build. For information on how to do this, refer to Unity Cloud Build.
- Create a new Mac Desktop build target in Cloud Build.
- Return to the Config page. This page now includes the Notarization section. Open this section and click EDIT NOTARIZATION.
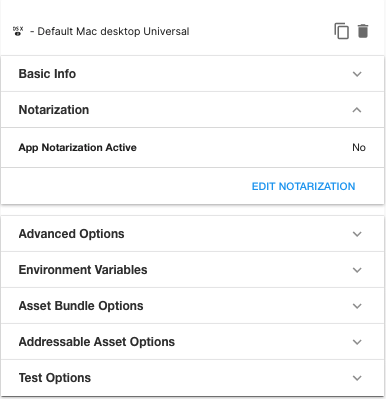
- Enable the Notarization flag. If you have previously supplied a set of notarization credentials to Unity Cloud Build for the same Organization, you can select those from Credentials. Otherwise, select Add new provisioning credentials.
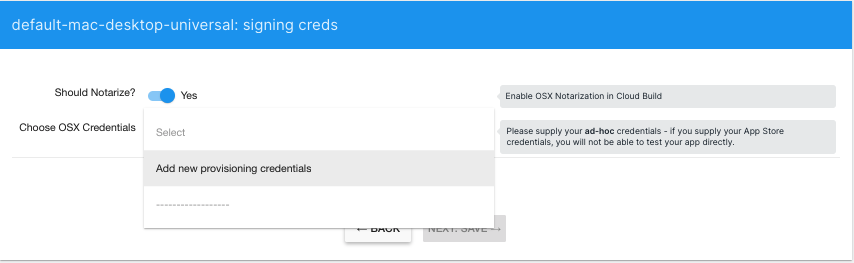
- Provide the following:
- Name: the name for your credentials set. You can use these credentials for any additional projects you set up in the same organization.
-
p12 File: The
.p12file you created in either Unity Cloud Build notarization for Apple devices or Unity Cloud Build notarization for Windows and Linux devices, depending on your platform. - Entitlements File (optional): The entitlements file you created in Notarization using Unity Cloud Build. If you do not provide an entitlements file, Unity Cloud Build uses the minimum entitlements a macOS application requires to have a Hardened Runtime. For information on what these minimum entitlements are, refer to Entitlements.
-
p12 Password: The password you supplied when you created the
.p12file. - Provider Short Name (optional): The provider short name you acquired in either Unity Cloud Build notarization for Apple devices or Unity Cloud Build notarization for Windows and Linux devices, depending on your platform. If your Apple ID is associated with more than one organization and you don’t provide this, notarization fails.
- Apple ID Username: Your Apple ID username.
- Apple ID Password: The application password you created in Notarization using Unity Cloud Build. Unity Cloud Build does not verify Apple credentials until it attempts to notarize your build, so make sure to enter the correct username and password.
-
Confirm your Apple ID Password: A repeat of the Apple ID Password.
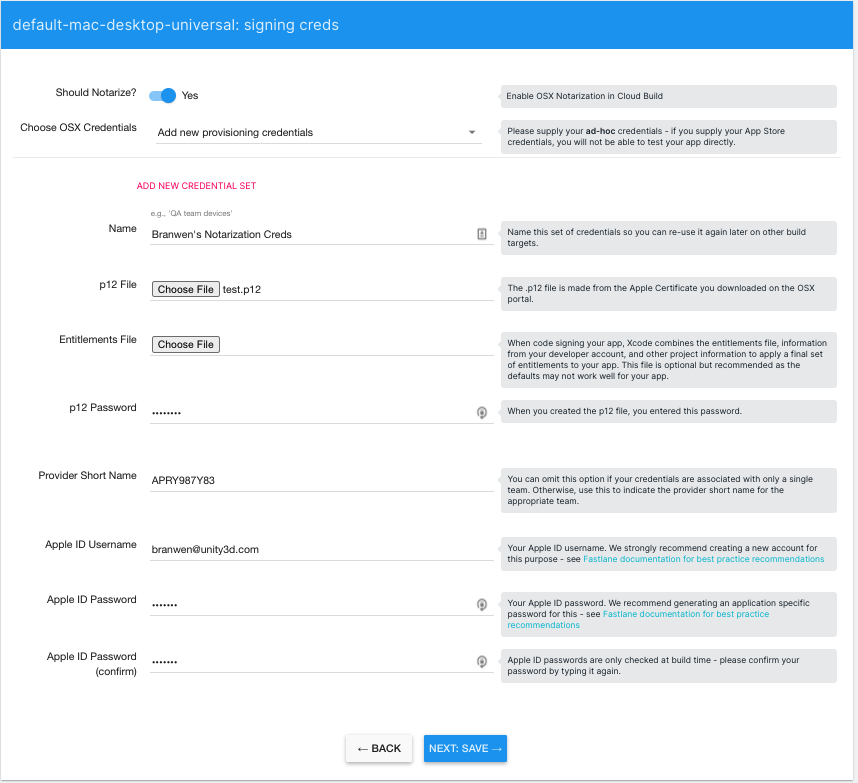
- Save your credentials.
- Return to the Build History page and start a build for your Mac target.
- If the build succeeds, Unity Cloud Build attempts to notarize and stable the result.
- Cloud Build runs the
codesigncommand with the following flags:--deep --force --verify --verbose --timestamp --options runtime. It’s not currently possible to specify custom flags. - Additional log outputs from notarization are available using the environment variable
FASTLANE_NOTARIZE_VERBOSE=truein your build target Environment Variables.
- Cloud Build runs the
- After Unity Cloud Build builds, notarizes, and staples your project, you can download a compressed file that contains the build.